Public Cloud
Public Cloud
Part 1. AWS-SSO Integrated with Azure AD
In this article I will show you how to create Aws SSO and integrate it with you azure AD for Single Sign on (SSO)
Many organisations have multiple public cloud providers. The challenge with cloud for many organisation is having a good mechanism on user access management (UAM). Many organisation have also integrated there LDAP into Azure AD , and while there are better Identity provider( IdP) Microsoft have made good improvements in this space.
Aws SSO is amazon alternative to Azure AD and has many connector to 3rd parties however in this senario we are going to put Azure AD as the primary and use AWS SSO to integrate with an AWS organisation.
Before starting you should have setup an AWS organisation if you don’t know how here a guide guide on how to set it up
AWS Config
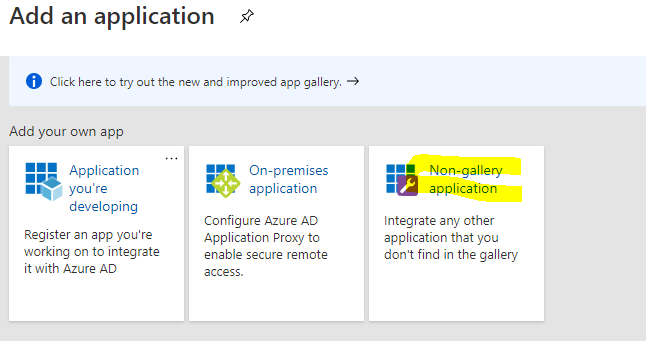
Login to you master AWS Organisation account and go to

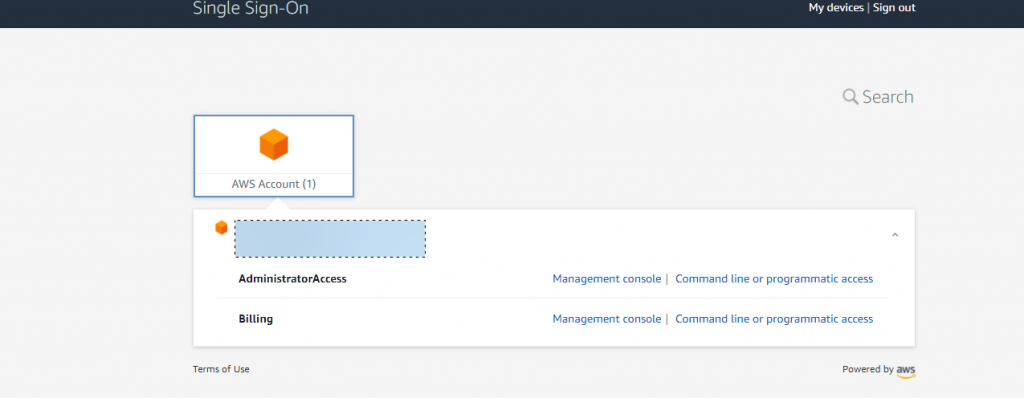
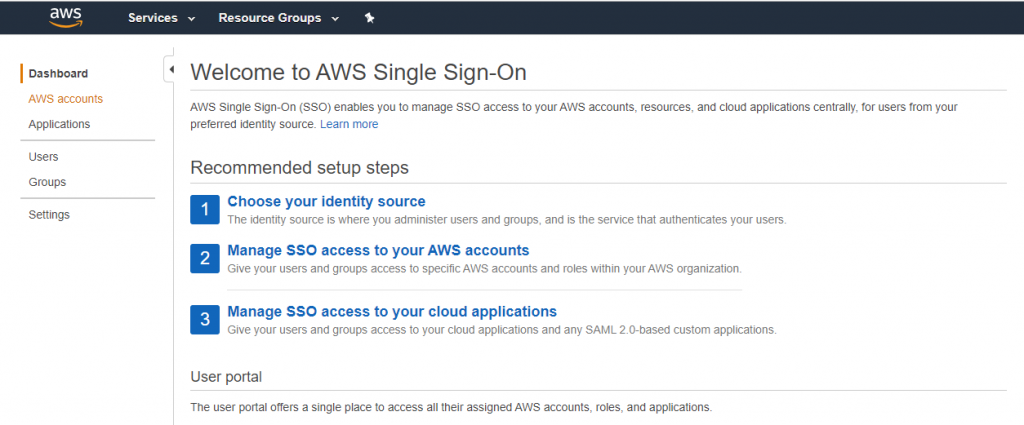
When you login you will get a screen like bellow

Click the Enable AWS SSO . In the background SSO is provisioned in each of the organisations accounts . you can see this but looking at the subscriptions IAM
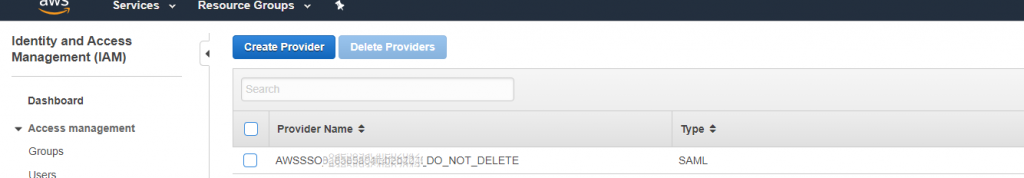
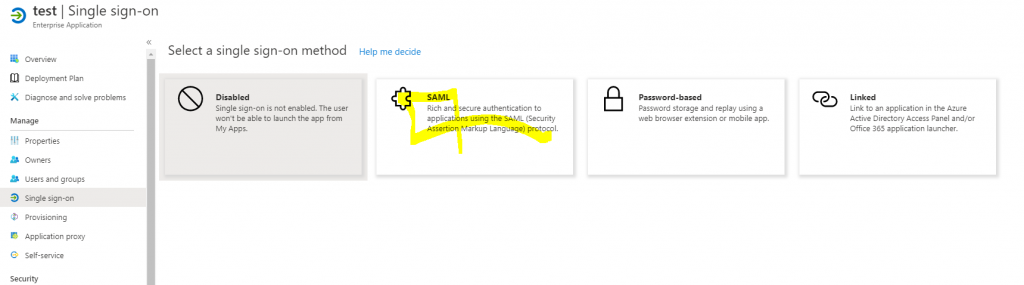
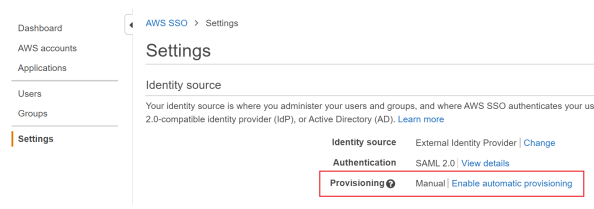
Once provisioned into SSO and click on choose Identity Source
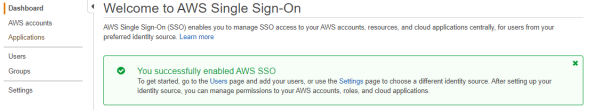
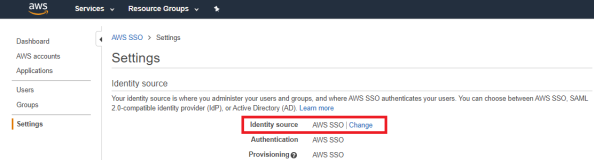
Click Change identity Source from AWS SSO
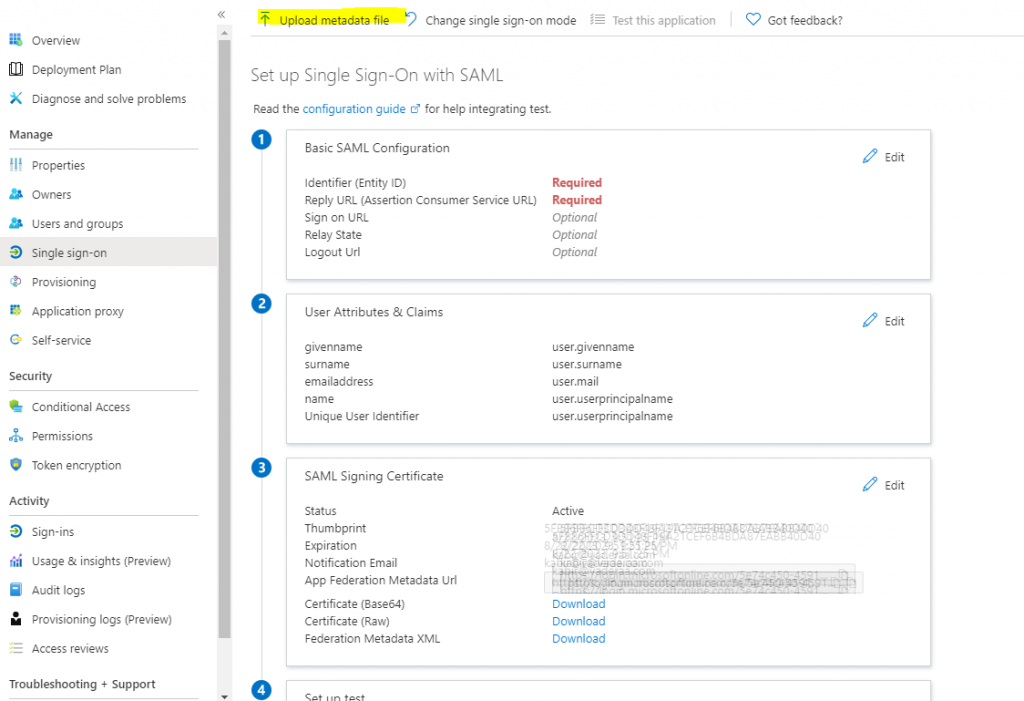
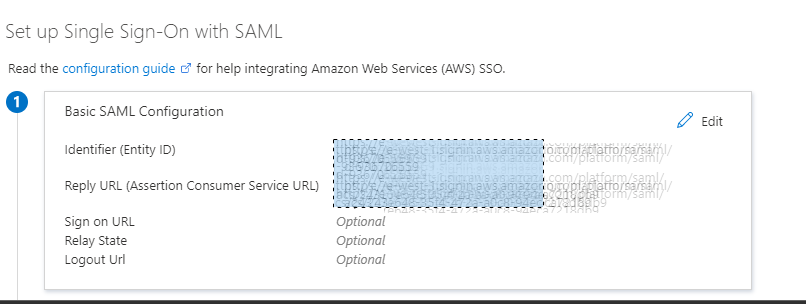
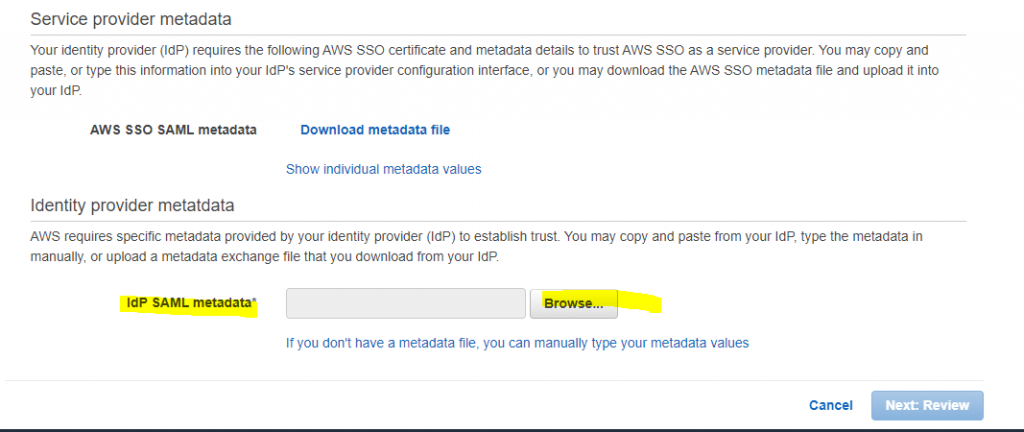
Select External Identity provider and download the metadata file.
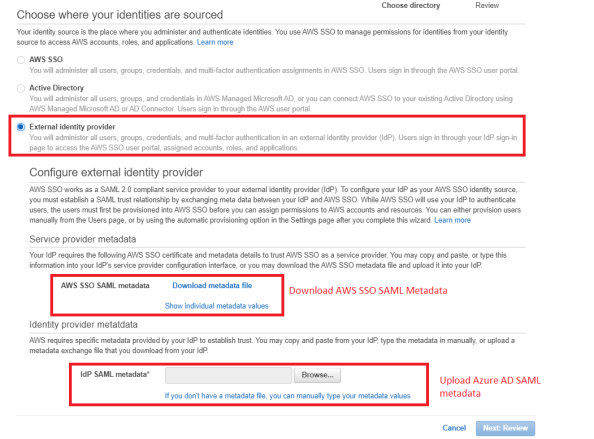
Next go to Azure AD Config Part 2